Hiding in Plain Sight: Using hidepid for Improved Privacy and Security
As a former Linux Sysadmin, I know the importance of privacy and security in multi-tenant systems. That's why I'm excited to share my experiences with using hidepid. In this post, I'll explain how it can help protect your data from prying eyes and keep sensitive information confidential.

When looking for ideas for a blog post, it's always a great feeling to look back and reflect on my early days in the IT industry. It all started almost ten years ago when I was a Linux Sysadmin at the University of Gdańsk in Poland. My role was to manage multiple academic servers and several Linux PC classrooms. During this time, I learned many valuable skills and tricks that I still use today.
One of the lessons I learned was how to use the `hidepid` kernel option to improve security and privacy in multi-tenant systems that we shared with students and academic professors. That was a handy tool, and I still use it to this day, so I'm sharing my experiences and knowledge with you in this blog post.
Hidepid
The hidepid function is a feature in the Linux kernel that allows you to hide the process information of other users on a shared system. It's convenient in multi-tenant systems, such as the academic servers and classrooms at the University of Gdańsk, where privacy and security are paramount.
The hidepid function changes the visibility of process information in the /proc file system. By default, all users on a Linux system can see information about all processes running on the system. Still, with hidepid, you can restrict this visibility to only the owner of the process or a specified group of users.
Three levels of visibility can be set with hidepid:
- 0 - Full visibility; all users can see all process information
- 1 - Restricted visibility; only the owner of the process can see its information
- 2 - No visibility; nobody except for root can see any process information
Implementing hidepid
Implementing the hidepid function is relatively straightforward. You need to add the following line to your /etc/fstab file:
none /proc proc defaults,hidepid=2 0 0Once you've added this line, you'll need to remount the proc file system to make it effective.
mount -o remount /procIn my experience, I typically used hidepid level 2, as it provided the highest level of privacy and security for our multi-tenant systems. With this configuration, only root could see process information, ensuring that student and academic data was kept confidential.
How does it look in practice?
This is how hidepid can limit the visibility of processes in the example of a virtual machine and htop.
Here is how it looks before applying:
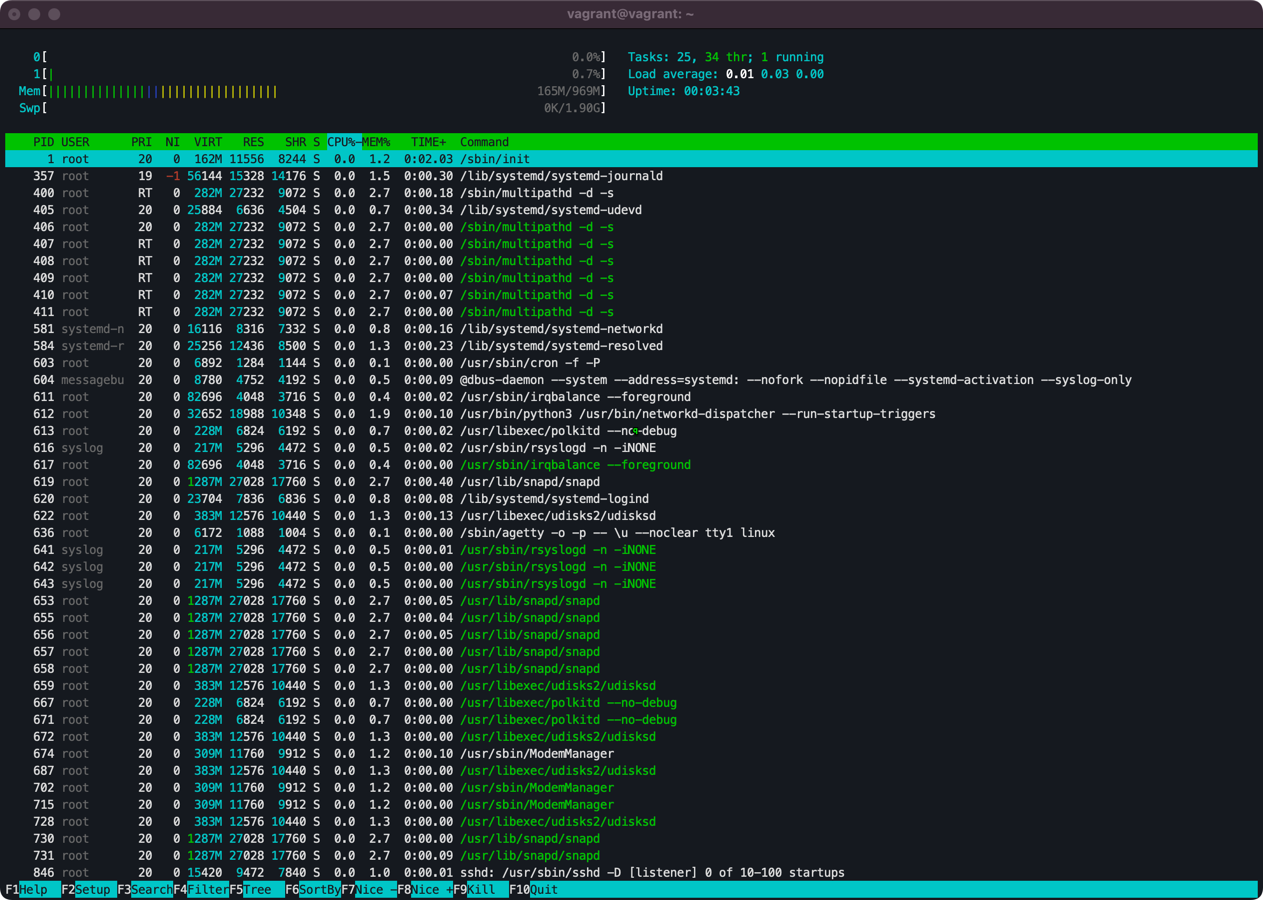
Quickly remount /proc with mount -o remount,hidepid=2 /proc , and this is the view again:
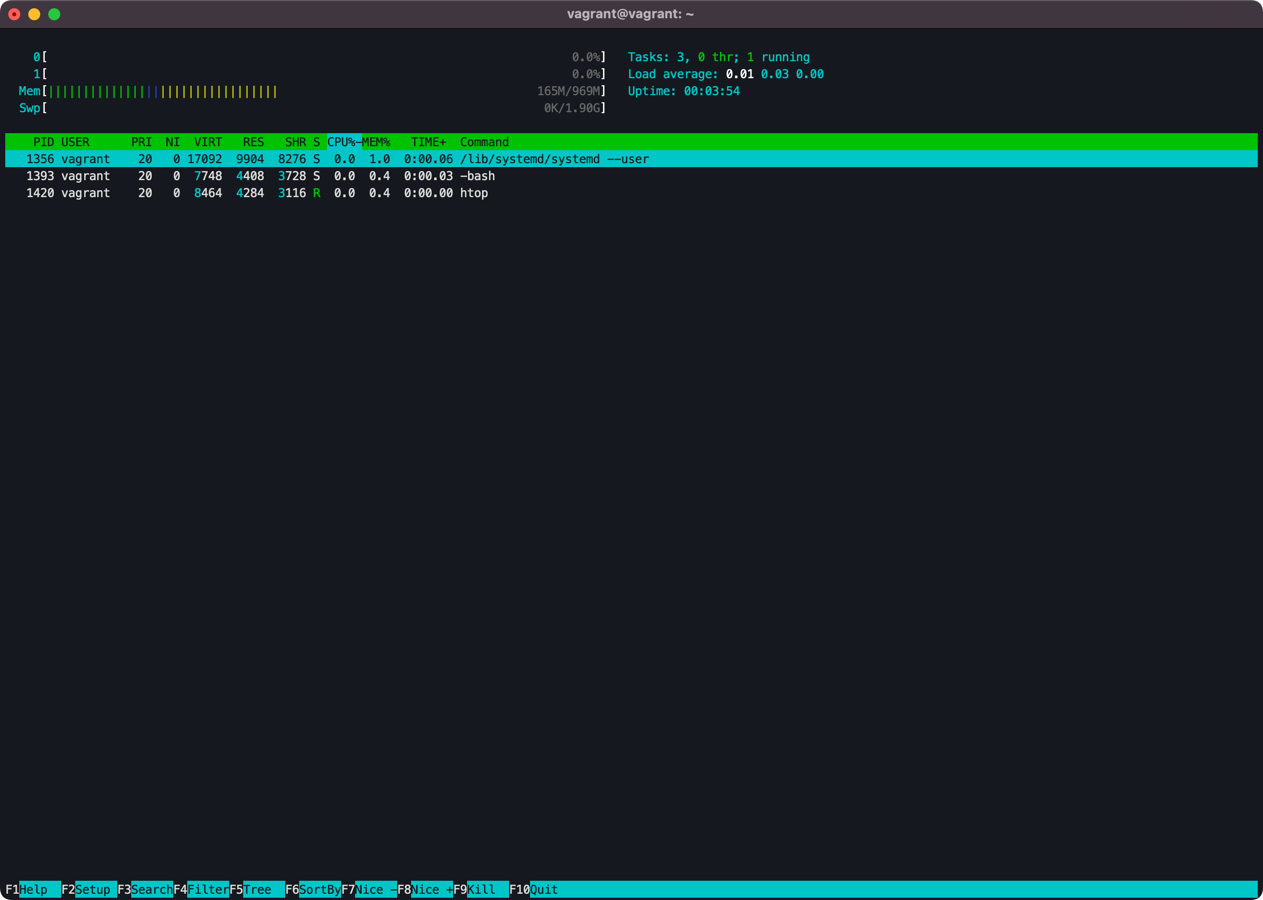
As you can see, the vagrant user can only see his processes in the htop overview. In the above example, it's only the bash session and htop itself.
Caveats
While the hidepid option is a powerful tool for improving security and privacy in multi-tenant systems, there are a few caveats to be aware of:
- Root User Visibility: When using hidepid, it's important to remember that the root user will always have complete visibility of process information, regardless of the hidepid setting. That means that if you have untrusted users with root access, they can see process information for all users on the system.
- Debugging and Troubleshooting: When using hidepid, it can be more challenging to debug and troubleshoot issues on the system, as information about processes running on the system will be restricted. That can make it hard to identify the root cause of problems and find a solution.
- Compatibility: Not all tools and applications are compatible with the hidepid option, and some may not work as expected when hidepid is used. It's essential to thoroughly test your devices and applications before deploying hidepid in a production environment.
- Performance: The hidepid option can impact system performance with many processes, as the information must be filtered and restricted. This can result in slower performance and increased resource usage.
Alternatives
While hidepid is a powerful tool for improving privacy and security in multi-tenant systems, it's not the only solution. Some alternative methods to hidepid include using containers or virtualization to create isolated environments for each user or group. This approach provides even greater user separation and privacy but can be more resource-intensive and complex to manage.
See one of my previous posts for more info:

Another alternative is to use SELinux or AppArmor, which are security modules that can be used to restrict access to system resources based on predefined rules. These modules can provide fine-grained access control but require a significant amount of configuration and management.
Ultimately, the best solution will depend on your specific needs and environment. It's essential to evaluate each option carefully and choose the one that provides the best balance between security, performance, and manageability.
Conclusion
The hidepid option is a handy and easy-to-use tool for sysadmins to improve privacy and security in multi-tenant Linux systems. I still use it to this day, and I highly recommend it to anyone looking to implement a similar solution in their designs. Stay safe!